
IT security
Navigation systems are easy prey for hackers
Drivers have almost blind faith in GPS. If hackers attack the system, they can cause great damage. The work group Information Security researches into defensive measures.
Hannelore Kraft, Minister-President of North Rhine-Westphalia, was deeply impressed when, in summer 2015, Junior Professor Christina Pöpper demonstrated how easily hackers can manipulate the Global Positioning System and, consequently, every other navigation satellite system as well. The visit took place during the politician’s annual summer trip, in the course of which she got an insight into the current status of IT research at the Horst Görtz Institute.
In their presentation given to the Minister-President, Christina Pöpper and her team simulated a car journey to her headquarters in Düsseldorf. Just like in real life, they entered the destination into the navigation device and started the application. Then, the surprise: even though the device did not leave the room, the position arrow started to move towards North Rhine-Westphalia’s state capital.
That was not caused by a software bug, but by an attack on the GPS, performed by the IT experts. They faked a trip that wasn’t actually happening. A scenario that attackers could feasibly manufacture during a real car journey, according to Christina Pöpper: “GPS has been in use since about 1992. Since 2002, we have been aware that it is vulnerable. In the intervening years, many countermeasures have been suggested, but as yet, no defence strategy has been developed that offers protection against all attacks. It always boils down to the question: how strong is the attacker?”
US Navy doesn’t trust GPS anymore
The severity of the problem is evident in the fact that even the US Navy does not fully rely on GPS. In 2006, GPS-based orientation replaced celestial navigation in their curricula – until recently. According to the Navy, the security and failure risk of GPS is so high that its officers are again being trained in the use of sextants. “I was surprised when I heard that. After all, we often assume that the military sector is more technologically advanced than the civil sector,” says Pöpper.

Together with her PhD student Kai Jansen, the computer scientist puzzles over a solution of the problem. Getting rid of GPS is not a viable alternative. One of the system’s advantages is its outstanding versatility.
Satnavs in cars, in electronic tagging devices, in aviation and in mobile phones all deploy GPS. Because it is suitable not only for determining position, but also for synchronising time, the system is also widely used in the industry for temporal alignment of machines and measurements.
The calculation of time with the aid of GPS is based on the technology’s underlying principle: in order to determine its position, the receiver measures the exact time a signal takes to travel between several satellites and the receiver itself. The number of satellites circling the Earth in high orbit exceeds 24. In every location on Earth, users make contact with at least four of them. The satellites continuously transmit their precise orbit parameters in their signal. Thus, the receiver knows exactly where the signal is coming from.
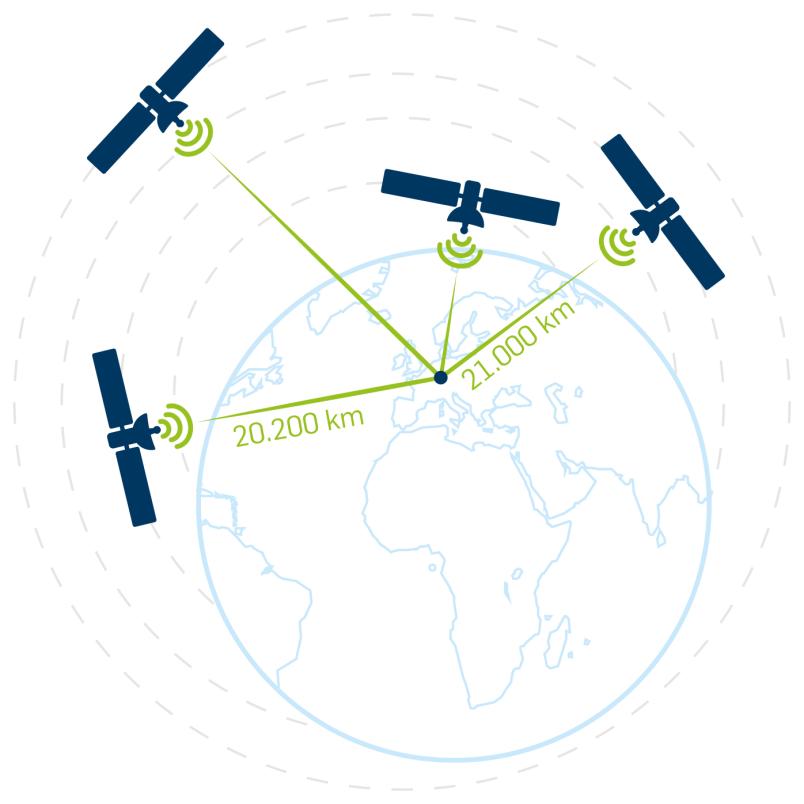
Moreover, each satellite has an atomic clock on board and can indicate the precise time when its signal was transmitted. The further from the receiver the satellite is located, the longer it takes for the signal to arrive.
Based on the known parameters, i.e. transmission time and transmission location of the four satellites, the location of the receiver is identified – this process takes place while the receiver’s local time is simultaneously determined.
Manipulation through satellite simulator
If an attacker wants to manipulate the system, he can use a satellite simulator for the purpose. The handy box, which the IT experts from Bochum also use for research purposes and which is routinely used for testing GPS receivers, generates satellite signals and transmits them via an antenna. The signals fake authenticity so well that most receiver devices do not notice any difference: a circumstance that attackers may use to persuade the receiver that it is situated at a different location than its actual one.
This vision is bound to make many people think of horror scenarios, such as hijacked airplanes, misrouted armoured cars or electronically tagged criminals disappearing underground.
Several receivers as solution
When proposing their solution, Christina Pöpper and Kai Jansen considered what happens when a vehicle or a machine uses not one but several receivers at the same time, which are situated at a distance from each other. If they receive genuine satellite signals, the receivers’ calculated position data differ slightly from each other, reflecting the difference between their actual positions.
If, however, an attacker transmits signals using a simulator, they appear deceptively authentic and are identical for each individual receiver. The attack can only be detected by comparing the individual receiver locations to each other, because now all receiver devices believe to be in the same (wrong) position, which is not actually the case.
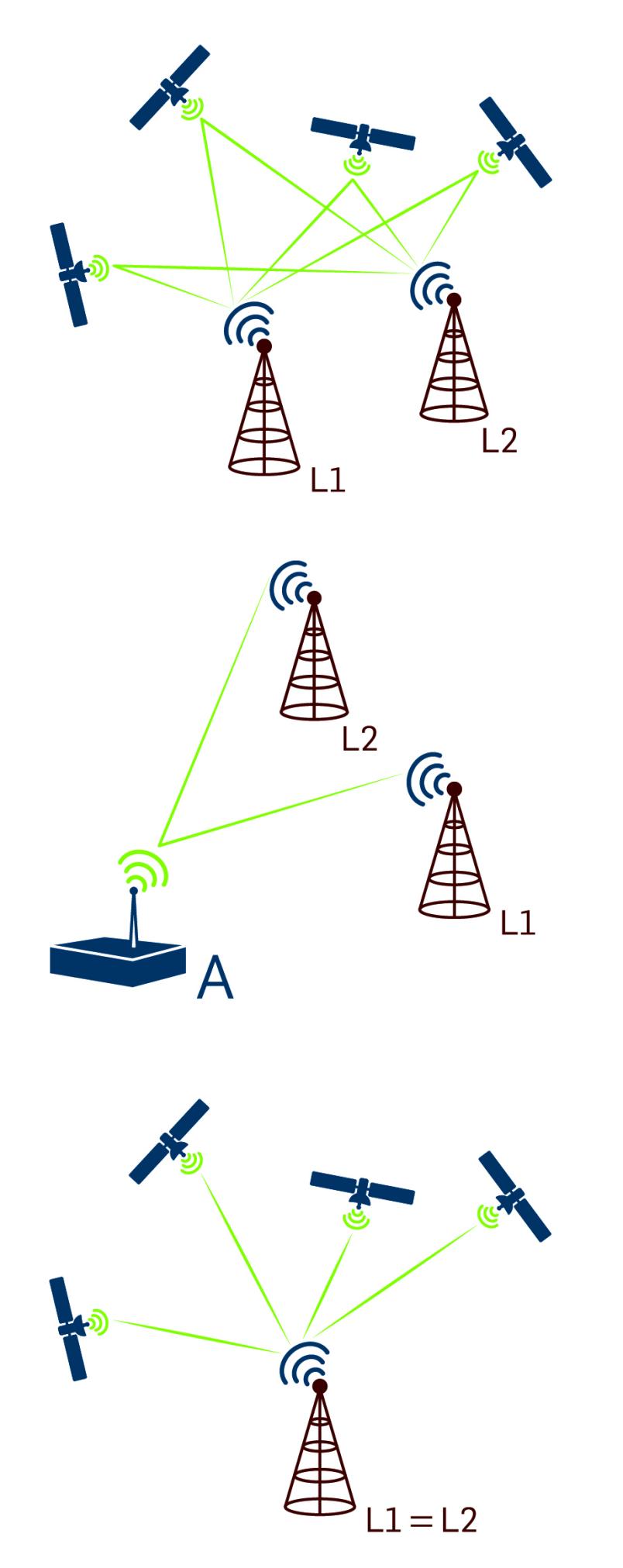
This is because the relative reception times of several signals which are transmitted via the satellite simulator are identical in several receiver devices. This is not the case when legitimate satellite signals are received, because they are transmitted from different positions in earth orbit.
“We have already demonstrated that this is how we can detect attacks. At present, we are figuring out technical details, such as the minimum distance that is required between the receiver devices to make sure that they don’t identify their positions as identical when receiving authentic signals due to inaccuracies that will inevitably occur,” says Christina Pöpper. In order to find that out, Kai Jansen took the trouble to climb to the roof of the IC building with his equipment, because signal reception is reliable here.

According to the current level of knowledge, the minimum distance between the devices should range between two and three metres. If the receivers are placed closer together, the error rate increases. “This can be easily realised in large vehicles or machines, such as trucks or ships, because here the receivers can be positioned at a sufficiently great distance from each other. However, this solution doesn’t apply in mobile phones, electronic tags or other areas.” This is reason enough for Christina Pöpper and her team to continue their research in this field.
