
IT security
More rules for the intelligent household
Lights out, doors open, online orders out: in a networked home, everything is controlled by voice or by pressing a smartphone button. But so far little thought has been given to who should be able to press which buttons.
The reactions may have ranged from amused to amazed to indignant: when the first episode of the 21st season of the TV series “South Park” was broadcast in 2018, voice assistants were starting to work in many American households. With very different consequences: Some systems set their owner’s alarm clock to 7 a.m., others repeated obscene sentences, others added unusual or embarrassing objects to their users’ shopping lists. The makers of the animated series had put signal words such as “Alexa”, “OK Google,” and “Hey Siri” into the protagonist’s mouth – presumably deliberately – and thus activated the home assistants in various households. It was not the first time that Alexa and Co. had accepted voice commands from the television. Even a large fast food chain had already caused a stir because it had integrated the command to read out a Wikipedia article about a burger in a commercial. Voice assistants are not yet able to recognise exactly who is giving them commands.
Many users
“We are used to only having one user on a PC or mobile phone. In people’s homes, there are many users who sometimes even control many devices simultaneously,” says Maximilian Golla from the Horst Görtz Institute for IT Security at RUB. At present, however, the systems do not yet reflect this reality. In the Bochum-based Mobile Security Research Group, headed by Professor Markus Dürmuth, Golla is concerned with what access control for Internet-connected household appliances should ideally be like.

Together with colleagues from the University of Chicago and the University of Washington, he conducted an online user survey in the United States with 425 participants to determine people’s needs. The survey was preceded by several preliminary studies in which the researchers first ascertained the status quo.
They researched which smart home devices are currently on the market, what capabilities they possess and how access rights to them can be managed. “The access control mechanisms for the devices were simply adopted from PCs,” summarizes Maximilian Golla. “In rare cases, there is a guest group with other access rights in addition to the administrator or owner, who is allowed to do everything – but that’s it.”

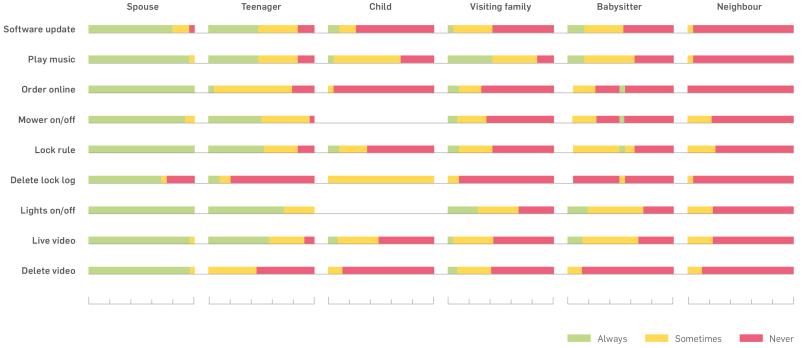
However, much more complex social relationships occur in a household than can be mapped by an administrator or guest role. In addition to the two spouses, for example, there may be children of different ages, family members visiting, babysitters, neighbours and others. “This is the real life that has to be depicted,” says the Bochum-based doctoral candidate. In addition, one of the initial findings of the preliminary studies was that it does not make sense to work at a device level; instead, the individual abilities of the smart home objects must be considered. “A voice assistant can play music, but can also shop on the Internet,” Golla explains as an example. “A child might be allowed to do the former, but not the latter – or perhaps only make purchases up to a certain value.”
Online study on user preferences
Among other things, the researchers looked through the user manuals of networked lighting systems, lawn mowers, thermostats, voice assistants, security cameras and door locks, and compiled a list of capabilities that smart home devices can have. In their online study, they then asked participants who should be able to control which of these capabilities.
They investigated six types of users: spouses, eight-year-old children, 16-year-old teenagers, visiting family members, babysitters, and neighbours. For 22 capabilities, they asked questions using the following template: “Imagine owning a voice assistant that allows you to shop online. When should your spouse be allowed to use this feature? Always, sometimes or never?”
It depends on the context
If a respondent answered “sometimes”, they had to specify how it would be determined whether or not the person should be able to use the function. From these responses, the researchers derived a number of contextual factors that affect access rights, such as age, where the person or device is located, whether the person has used the device before, the time of day, and the cost of using it.
Lastly, the participants in the study gave details of how unfortunate it would be if a user were denied access to a capability under certain circumstances. “If you’re standing in front of a door and can’t get in, it’s bad,” Maximilian Golla explains. “If you’re sitting in your living room and can’t shop via your voice assistant, it’s not the end of the world.”

It is not enough to have an admin role and a guest role within access control.
Maximilian Golla
Using all the data from the survey, the IT researchers created a profile of the capabilities that each user group should be able to use by default. Spouse and neighbour represent the extreme positions: according to the study participants, the spouse should have almost all rights, the neighbour almost none. For the other user groups – teenagers, children, visiting family members, and babysitters – there were four different combinations of desired and undesired capabilities. “This makes it clear that it is not enough to have an admin role and a guest role within access control,” summarises Maximilian Golla. “It must be possible to make much finer gradations and deal with the factors that mainly influence whether access should be granted or not.
Deriving default settings
However, it is also important that the system is not so complicated that the users of Internet-connected households no longer want to deal with the plethora of access restrictions. “We therefore concentrated on six user groups in the study,” explains Golla. “The data collected can be used to derive standard settings for these roles, which the user would then only have to adjust if necessary.” The settings should also allow for the extremes, says the researcher. “It should not happen that someone stands in front of the door and cannot come in, or that he or she is in the house and cannot switch on the light.”
Maxmilian Golla refers to an aspect that the study did not explicitly deal with: “Of course, there is still a back door,” he says. “If I can’t switch the light on via my smartphone, then I just go to the switch and press it. Many of the devices we’ve dealt with still exist in the real world, and access to them cannot be completely limited to software.”
Rule language for implementation
Nevertheless, digital household control will certainly become more and more popular. For this reason, Maximilian Golla and Markus Dürmuth’s American cooperation partners are already working on further studies on how the allocation of access rights could work in practice. There are already hubs that can be used to centrally control all networked household appliances. It should also be possible to assign access rights to all household functions at the same time. “For example, the role ‘child’ would be assigned to a person who has certain standard settings,” describes Golla. “This would then determine the rights for all networked devices and their functions.”

All kinds of desired processes in the home could already be automated today with a rule language – called “If This Then That”. The language shows commands according to the formula “If case A occurs, then do B”. For example: If the purchase is cheaper than 20 euros, send out the order. Or: If it is between 3 and 5 p.m., switch on the TV.
In the future, the researchers want to investigate how this kind of rule language could be used to manage access restrictions for the everyday functions of the smart home devices in a user-friendly way.
